Case Management
Blackthorn Case Management solutions offer our clients flexibility, ease of use, integration, choice of risk management methods, better reporting, security and accuracy. At Blackthorn, we follow “listen> improve> repeat” approach that helps us in reducing your costs and risk across your enterprise.
Case Management Solution
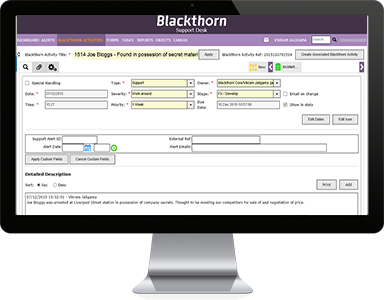
Our CMS is a web-based solution used for Public Sector, Banking, Military and Aerospace. Whether in the field of forensics, criminal, fraud, or vetting, Blackthorn is a tried and tested system that enables clients to manage their workload with total security, integrity and accountability. Access to your information is based on your role within your organisation. We also have Special Handling for when you need to investigate internally. When you capture information that is crucial for your process, that data will be hashed to ensure that no one can tamper with it, so you can be confident that when it is retrieved it has not been altered in any way. A full audit log of all user activities provides high levels of accountability and transparency at the same time allowing your users to easily manage their cases.
Our Aim
We want you to have a solution that allows you to record, manage and report your case without getting in the way of your staff actually performing their work. Systems should make life easier, not something you have to fight with. We want to work with your organisation to make it more effective, staff happier, and at the same time be compliant with processes, resulting in better profits.
Our Features
All variants of our Case Management Solutions are based on a technological platform (cloud or on-prem) that incorporates the following features and capabilities. Click on a feature to find out more.
-
Information Capture High-fidelity eForms with embedded data validation and consistency checking help to eliminate mundane and error prone data entry. eForms are context sensitive, only displaying the fields required for the operation in-hand. Documents, files, audio recordings, scanned papers etc. can be emailed to the system and automatically added to a case. Web services allow data transfer (input and output) to other digitally enabled, online systems, again reducing the necessity for manual data entry (see Interoperability below).
-
Records Management Our Records Manager function provides real-time access to investigation records including evidence, statements, suspects, witnesses, strategy, and case progress. Case records can also hold uploaded artifacts such as documents, photos, audio recordings, video files etc. A graphical interface supports the organisation of this data, with subfolders for the classification of different types of case content. For example, statements prepared by subject matter experts could be archived in a dedicated subfolder under a case. There is no restriction on the file types that can be uploaded and appended to a case. Logical associations can be created between cases and the between records and artifacts across cases. For example, cases created to investigate a case of fraud within a given business function or service operation could be linked. The system can securely handle sensitive information and restrict access to only those with a genuine ‘need-to-know’.
-
Search A Search function employing 'fuzzy logic' allows searches to be conducted with partial or incomplete data. During data entry or file upload, the information presented to the ICM system is indexed prior to storage, creating meta-data files that accelerate future searches and look them up. The search results remain vigilant of any user access restrictions in force, ensuring the privacy of sensitive information.
-
Dashboards
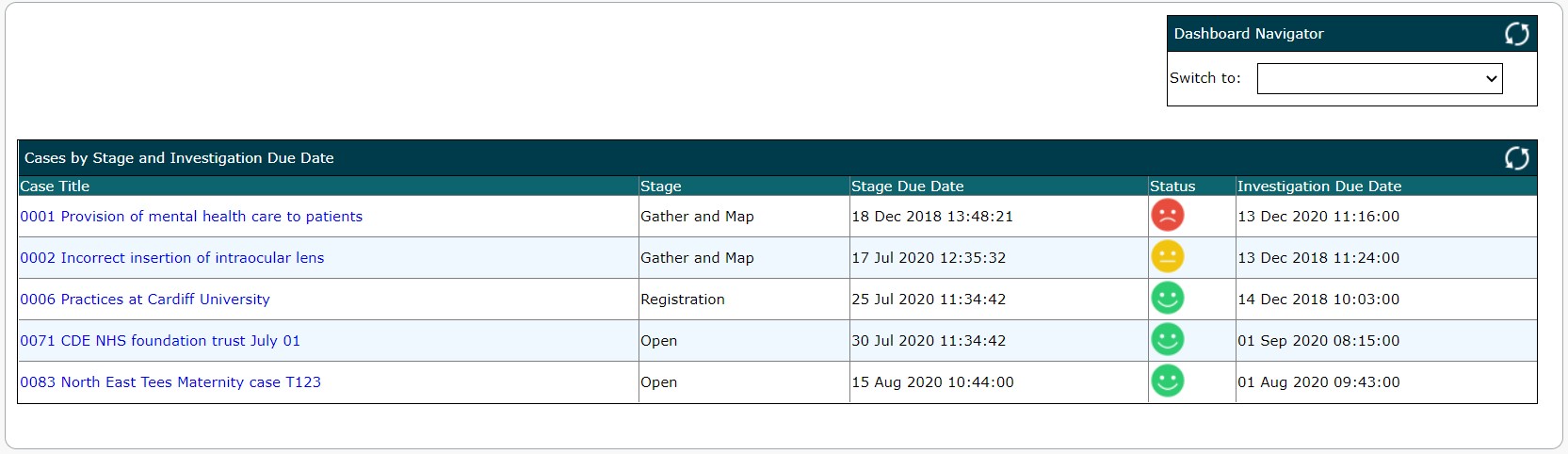
'At-a-glance' access to key information and insight needed to drive decisions. Operational dashboards provide directors, managers and seniors with a snapshot of the status of operations including capacity and progress. They provide investigators with fast-changing information about their cases, workload, actionable tasks, overdue activities etc. Analytical dashboards enable a more detailed evaluation of cases, comparison between cases or over time, or access to underlying details or trends. An example of a dashboard is provided in figure 2 & 3 below.
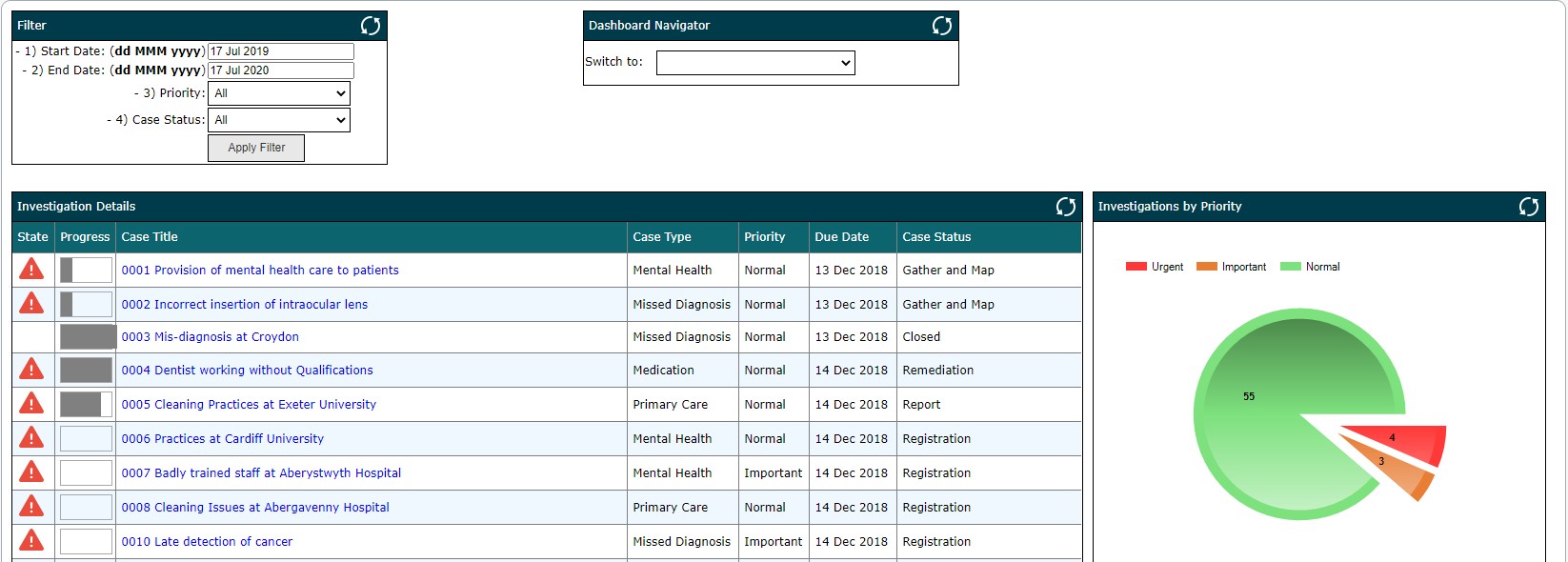
Filtering by case attribute, for example investigator, team manager, reporting date, investigation status, etc. allows the 'window' onto case data to be narrowed and better focused. Filters can be also used for analytical reporting and detailed trend analysis.
Our ICM is supplied with a range of standard, pre-configured dashboards which can be retrospectively and individually fine-tuned using filters and personal preferences. Custom dashboards can also be created (permissions allowing) to meet a specific, individual business needs. A graphical interface and a range of standard widgets (standard dashboard components) is available for this purpose.
-
Forms & Reports
Tool support for the creation of forms (.docx) and reports required by statute, regulation, policy and internal protocol. Document templates can be added to the library of supplied templates allowing standard and bespoke forms and reports to be created digitally and auto completed with relevant case data. All system created documents can be annotated by the user before completion, allowing subjective content to be added. Documents can be saved against a given case or to other (external) locations. Edit access to the library of standard document templates can be locked down to specific, authorised users.
-
Data extraction
Data export (in either .xlsx or .csv file formats) is supported by a 'wizard' giving users complete control over the extraction process. This function might be used to facilitate statistical data analysis outside the standard analysis and reporting that is integral to the ICM system. The wizard also provides the ability to navigate around dynamic database content and structures.
-
Tasking & Workflow Workflow allows a set of actions with a defined outcome to be defined, organised and accomplished in prearranged order. After an assessment, typically there are a number of follow-up activities (tasks) that must be completed within a set timeframe; some of these tasks are related and interdependent and require completion by two or more people, possibly even external departments or agencies. Workflow coordinates the conduct of such tasks, sequencing as appropriate; the work only commencing when conditions allow. Task owners are notified at the appropriate time and reminders are issued before, at, and after the ‘due date’ if the task is late.
Whilst 'Tasking' is integral to the Workflow function, additional 'ad-hoc' tasks can be created as part of workflow, or independently, to address the specific and often unique needs of an investigation case. Work activities and tasks can be dynamically assigned to members of the investigation team or a wider group. Tracking tools provide fully visibility of the status of tasks, including child tasks, highlighting lateness and/or overrun. Workflow definitions are created and published by users with administrative user privileges using a graphical user interface and drag and drop functionality.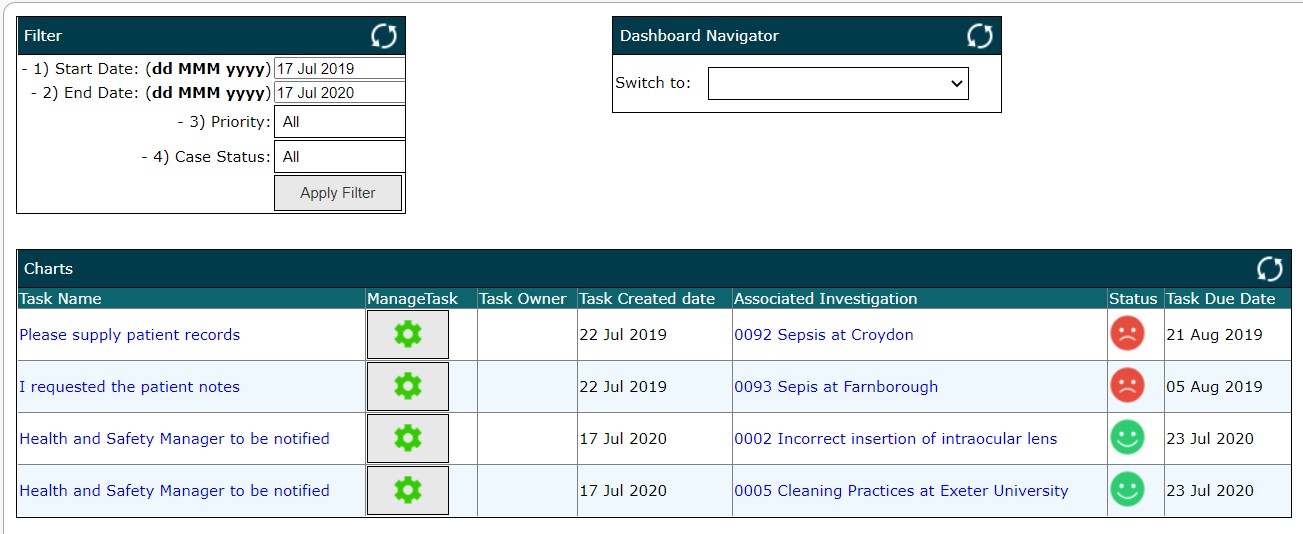
-
Case Allocation
Case records have a number of attributes that are used solely by the ICM system. The 'Pool' attribute allows investigation case records to be segregated into sub-groups (i.e. pool 'A', pool 'B' etc.) and access to a sub-group restricted to a specific group or community of users. The most obvious benefit of pools is the ability to establish Chinese walls between different investigation teams or between business functions. Conversely, pools can be used to widen access, giving individual users or groups of users, access to case records (i.e. cases with a common pool ID) that previously they might not have had visibility or access to. The segregation of users might be appropriate where two or more departments are using a single ICM platform for different types of investigation (with different privacy requirements), or where the sensitivity of investigations means that access must be locked down and restricted to a specific cohort within a wider investigation team. Pools also allow new investigation cases to be initially allocated to an 'unassigned' category. Often some basic, rudimentary information needs to be gathered and evaluated before the true nature of events leading to the investigation is known. The unassigned category affords this opportunity, allows time to properly establish 'what' and 'when', and 'how' and with 'whose' oversight the investigation can best be moved forward. At this point the case can be allocated to a team (specific pool ID) and assigned an owner.
-
Alerting and Notification
Multiple channels are available for alerting and notification. Dashboards provide assessors, team leaders, managers etc. with details of actionable tasks awaiting attention. The task list can be case centric or list actionable tasks from all cases assigned to an individual. Email alerts and notifications can be triggered manually or by workflow, raising awareness without the need to log-on. Internal messaging is a succinct method of communicating with other ICM users and has the advantage of keeping the content of the communication within the confines of the system (avoids possibility of data leakage or creep).
-
Collaboration and Communication Management
Effective collaboration depends on good team communications but a team operating without accountability is unlikely to collaborate in a helpful way. A centralized database and Role-Based Access Control (RBAC) ensure case records are reachable, and access controlled, with segregation based on an individual user’s profile and team hierarchy. The ability to assign access privileges to individual data assets further enhances access control, increasing the level of granularity and allowing access policy to model extant team, department, office or regional hierarchical structures. Accountability is enforced by user rights and permissions but also the process management paradigm embodied in the implementation (a function of configuration and setup). All user actions are logged providing an admissible record of system and user actions. Log entries cannot be deleted or amended. This audit trail helps enforce accountability.
-
Compliance and Data Retention (GDPR)
Compliance is a key issue for all organisations, be it regulatory, legislative, or alignment with internal policies, procedures and rules. Compliance is addressed in a multitude of ways:
Workflow ensures authorised processes are followed
Changes to records, evidence and internal communications are evidenced by an auditable digital record, and
Strong user account rights ensure effective segregation of duties.
-
Interperability
A library of pre-existing web services (Open API compliant and RESTful) are available for standard interfacing needs. OLEDB services are available allowing direct interaction with our data storage medium. Additionally, data can be exchanged digitally via email - both inbound and outbound. This has many advantages as SMTP, the vehicle enabling email, is ubiquitous, making it a very open and accessible channel for information exchange.
Other Blackthorn Features Include:
lay down, in advance, workflow (repeatable patterns of activity) aligned to the optimum response strategy for a given investigation type (e.g. fraud, theft, sexual harassment)
define, capture and publish ad-hoc response strategies for extraordinary investigations (i.e. investigations not presently catered for)
log key decisions regarding determination of strategy and information that informed decisions
Secure Reporting capabilities supporting individual and collective case analysis
Graphical modelling to help visualise linking people, locations and evidence
Contemporaneous (Write once, Read many) notes available at multiple points in a case's life cycle
Ability to assign, track and chase key responsibilities via Task Management
Update cases and attach evidence simply by sending in an email